Correlation Filters
ELM Correlation Filters are used only by ELM Correlation Views. These Filters are designed to watch for the ending event in a pair of correlated events. The Correlation Criteria can be hardcoded, or can use environment variables which resolve to values found in the Start events. In addition, the Message field can use regular expressions to allow sophisticated filtering patterns when watching for pairs of correlated events.
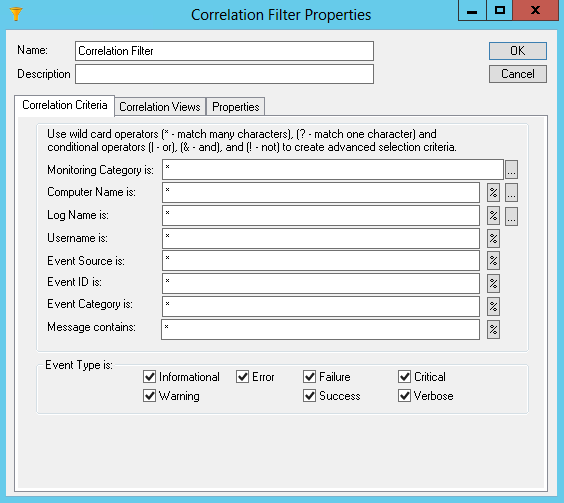
| • | Name – Enter a unique name. |
| • | Description – Enter a description (optional). |
Correlation Filter Criteria
Correlation Filters provide a mechanism for isolating specific events, and multiple Correlation Filters can be combined to create a complex set of criteria. The same Filter can include or exclude events.
The following fields are available for filtering purposes:
| • | Agent Category is |
| • | Computer Name is |
| • | Log Name is |
| • | Username is |
| • | Event Source is |
| • | Event ID is |
| • | Category is |
| • | Message contains |
This dialog box has a dynamic menu behavior. The ellipsis button next to the Agent Category, Computer Name, and Log Name fields browse and display the agent category names, computer names, and event log names. If the Computer Name field is left blank, the list of event Logs and Sources is generated based on the event sources registered on the ELM Console computer (i.e., the local computer). If you enter a valid, resolvable name in the Computer Name is field and then click the ellipsis button for the Log Name or Event Source fields, the list of event Logs and Sources from that system will be displayed.
Environment Variables
The percent button for most fields will put the matching environment variable in the field. This variable will use the value from the "start" event and look for a matching value in the "end" event.
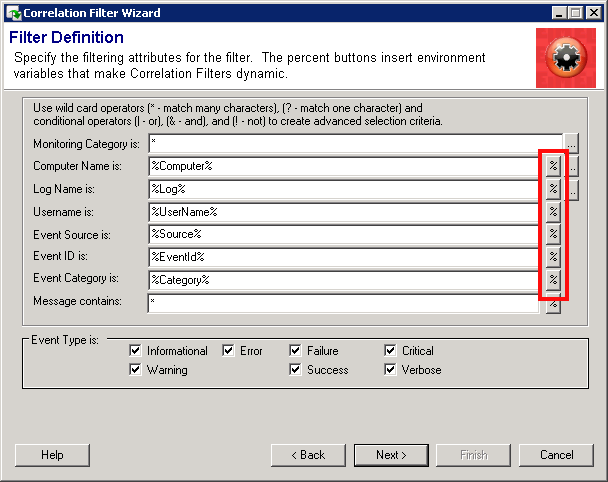
The Message field can use a variety of environment variables. Like the other fields, the environment variable takes the value from the "start" event and looks for that value in the "end" event. Additionally, it can use a custom regular expression match variable for advanced match criteria.
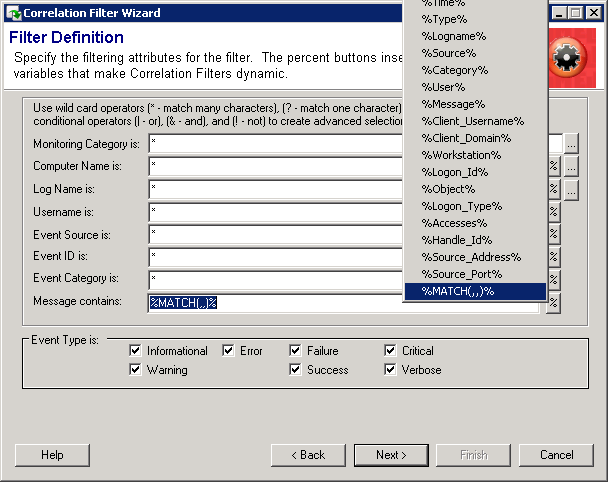
The MATCH variable uses the ECMAScript grammar provided by TR1 Regular Expressions. Microsoft documentation can be found here: http://msdn.microsoft.com/en-us/library/bb982727.aspx. Inside the parentheses, the MATCH variable requires 3 parameters:
1.A regular expression to capture a string from the "start" event
2.Reuse of one or more strings to look for in the "end" event
3.True or false, require case sensitive matching
For example:
%MATCH("username: (.+)","\0","false")%
This match pattern searches for a "start" event that contains "username" followed by a colon, a space, and one-or-more characters. The one-or-more characters pattern (period followed by a plus-sign) is inside parentheses, so these characters are captured. These captured characters are reused by the 2nd parameter via the \0 characters. So the "end" event must have the same username. The 3rd parameter (false) makes this match case in-sensitive.
Another example:
%MATCH("handle id:[:blank:]+([:w:]+)","handle id:[:blank:]+\0","FALSE")%
This match pattern searches for a "start" event that contains "handle id" followed by a colon, one-or-more blanks (spaces or tabs), and one-or-more alphanumerics. The one-or-more alphanumerics pattern (open square bracket, colon, w, colon, close square bracket) is inside parentheses, so these characters are captured. These captured characters are reused by the 2nd parameter via the \0 characters. So the "end" event must have "handle id" followed by a colon, one-or-more blanks, and the same handle id value as the "start" event. The 3rd parameter (false) makes this match case in-sensitive.
A 3rd example:
%MATCH("The (.*) service .* stopped","The \0 service .* running","FALSE")%
This match pattern searches for a "start" event that contains the letters "The" followed by a space. Then it captures everything upto a space followed by the letters "service" and followed by another space. Then anything, followed by a space, and followed by the letters "stopped". The end result is the name of the stopped service is captured. These captured characters are reused by the 2nd parameter via the \0 characters. Similar to the first parameter, the 2nd parameter looks for the service name followed by the word "running." The 3rd parameter (false) makes this match case in-sensitive.
Note: Regular expressions are supported only in the custom MATCH variable in the Message Contains field.
Leading and trailing wildcards ( * ) and character position wildcards ( ? ) are supported, as are the Boolean operators Or ( | ), And ( & ), and Not ( ! ). You may use these wildcards to specify the criteria to be applied. For example, to select messages from SQL Server you may specify *SQL* as the event source to select any Source name containing the letters SQL. To match SQL messages from servers ALPHA, BRAVO, or CHARLIE you would enter ALPHA|BRAVO|CHARLIE in the Computer Name is field.
Important
Leave no white space adjacent to the operators.
Note
If you enter the name of an untrusted system in the Computer Name is field and then use the ellipsis buttons for Log or Event Source, the menus will not be displayed. This is because authentication fails. To work around this problem, first make an IPC$ connection to the target system using alternate credentials. For example, if the untrusted system's name is dArtagnan, you could use:
NET USE \\SERVERA\IPC$ /user:dArtagnan\administrator *
You will be prompted for the password for the account you specify. The dynamic menu behavior will work after the IPC$ connection has been established.
Correlation Views