Exclude Event Filters are common objects within ELM and can be assigned to Event Views, Security Views or Correlation Views to have specific events excluded from the View. In addition they can be assigned to Monitor item types Event Collector, Event Writer, Syslog * or SNMP * to exclude events from Agent collection.
The Filter criteria entered by the user controls what events are excluded from collection and displaying.
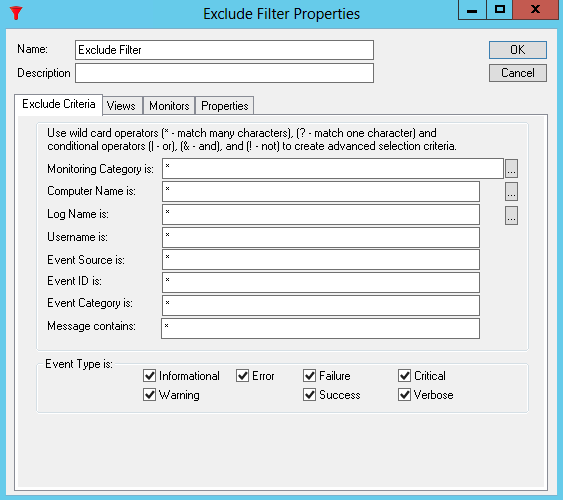
•Description - Enter a description (optional).
Event Filter Criteria
Event Filters provide a mechanism for isolating specific events, and multiple Event Filters can be combined to create a complex set of criteria. The same Filter can include or exclude events. They can also be created in the ELM Database Wizard to control database deleting or archiving, however these Filters will not be available in the Event Filter collections.
The following fields are available for filtering purposes:
•Agent Category is
•Computer Name is
•Log Name is
•Username is
•Event Source is
•Event ID is
•Category is
•Message contains
This dialog box has a dynamic menu behavior. The ellipsis buttons next to the Agent Category, Computer Name is, Log Name is, and Event Source is fields browse and display the agent category names, computer names, event log names and event sources. If the Computer Name is field is left empty, the list of event Logs and Sources is generated based on the event sources registered on the ELM Console computer (i.e., the local computer). If you enter a valid, resolvable name in the Computer Name is field and then click the ellipsis for the Log Name is or Event Source is fields, the list of event Logs and Sources from that system will be displayed. If the log or event source from which you want to collect data does not appear on the list, type it in the appropriate field. For example, if you are not running DNS on your ELM Server or Console, but want to collect events from the DNS log only, type DNS in the Log Name is field.
If a field is blank, it will match every value in the field. For example, if the Computer Name is field is blank, the Filter will apply to all computers. If all Event Types are unchecked when the Event Filter is saved, all of the Event Types will be checked. This is by design.
Leading and trailing wildcards ( * ) and character position wildcards ( ? ) are supported, as are the Boolean operators Or ( | ), And ( & ), and Not ( ! ). However regular expressions are not supported. You may use these wildcards to specify the criteria to be applied. For example, to select messages from SQL Server you may specify *SQL* as the event source to select any Source name containing the letters SQL. To match SQL messages from servers ALPHA, BRAVO, or CHARLIE you would enter ALPHA|BRAVO|CHARLIE in the Computer Name is field.
Important
Leave no white space adjacent to the operators.
Note
If you enter the name of an untrusted system in the Computer Name is field and then use the ellipsis buttons for Log or Event Source, the menus will not be displayed. This is because authentication fails. To work around this problem, first make an IPC$ connection to the target system using alternate credentials. For example, if the untrusted system's name is dArtagnan, you could use:
NET USE \\SERVERA\IPC$ /user:dArtagnan\administrator *
You will be prompted for the password for the account you specify. The dynamic menu behavior will work after the IPC$ connection has been established.
Views
Shows the Views associated with this Exclude Event Filter. Select New to create or Properties to edit a highlighted View.
Monitors
Shows the Monitor Items of type Event Collector associated with this Event Filter using an Include relationship. Right click to create or edit an Event Collector.